Handling SQL Error and Vulnerability BUG in JENKINS_job by SQLplus script runner plugin
How to make Jenkins job as failure for SQL errors (SQL syntax or any SQL Error):
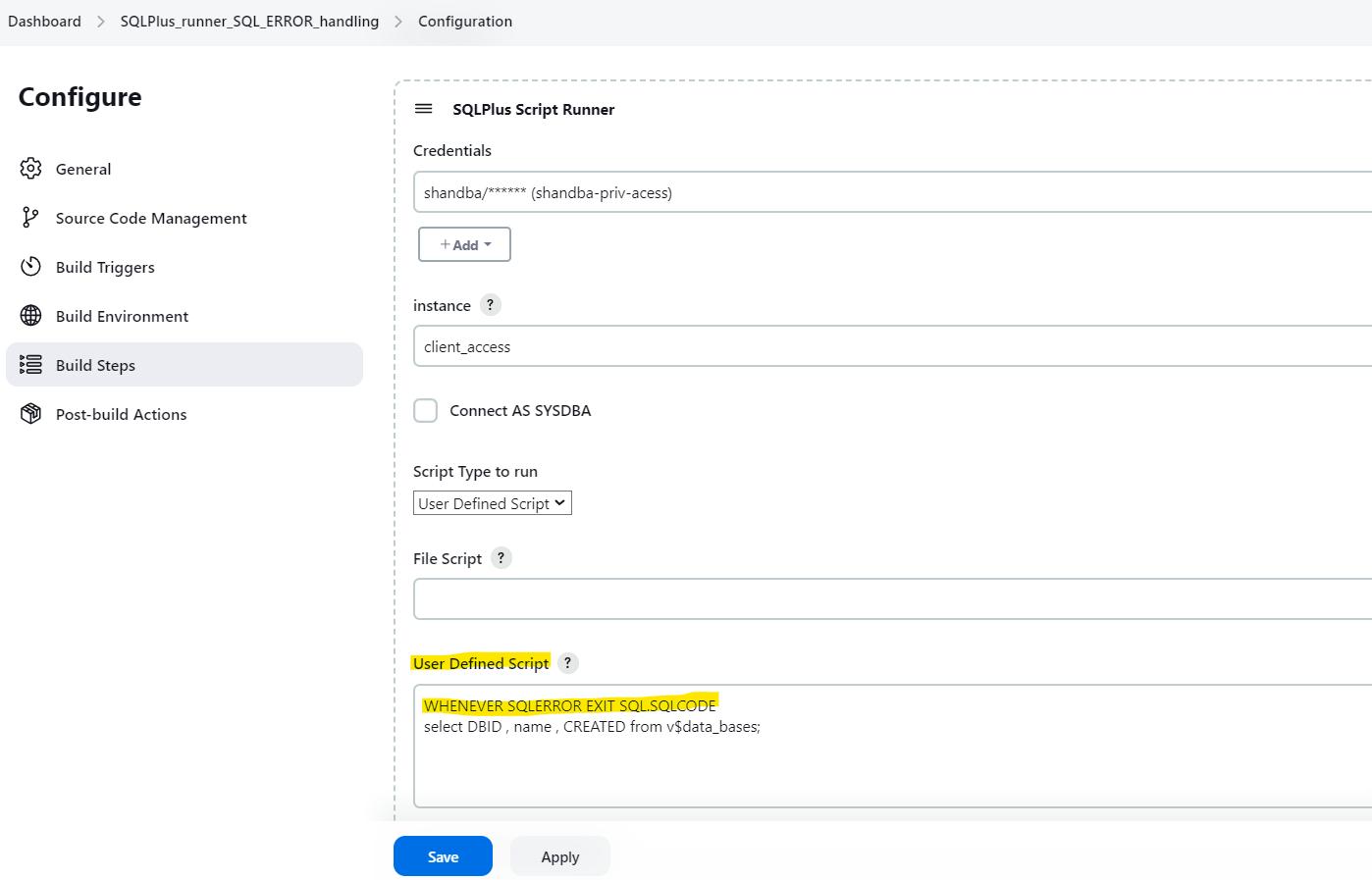
Add the additional code in Jenkins SQL file or SQL user defined code.
👉To check the SQL failure.
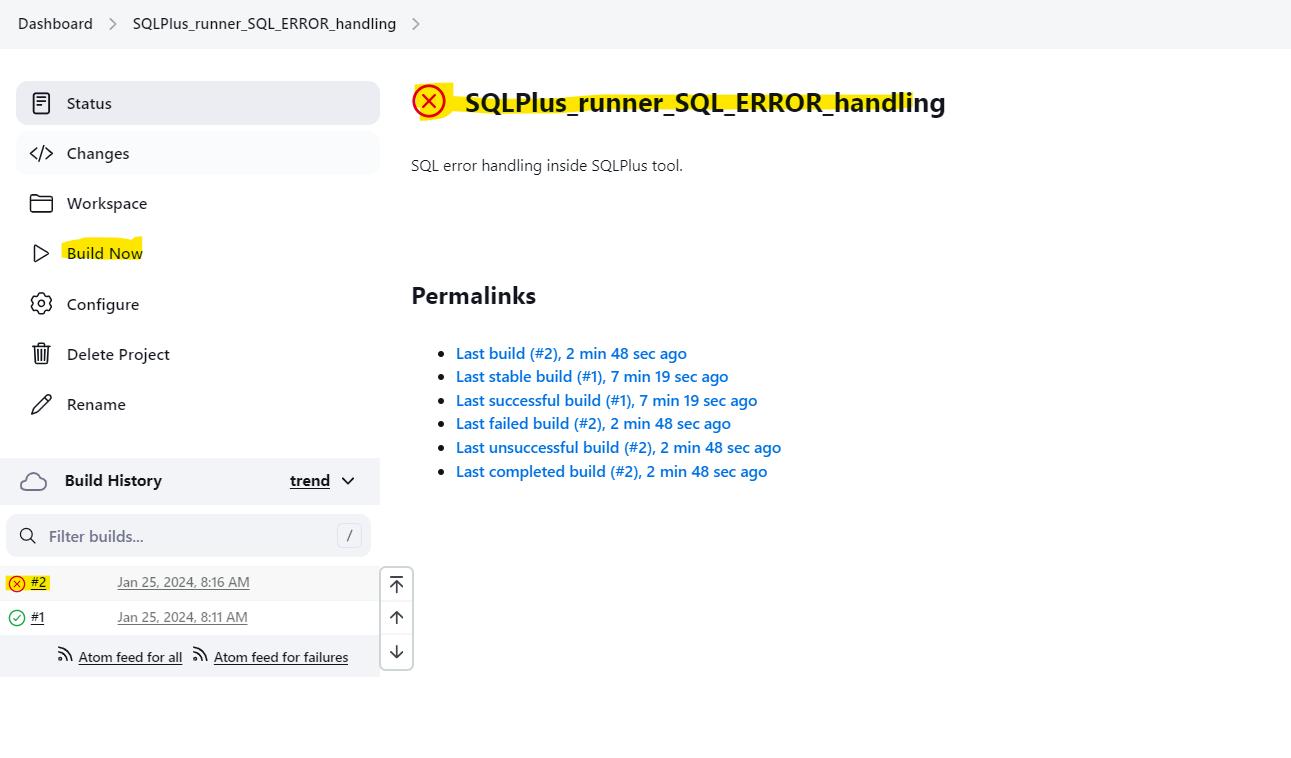
👉 Build the job and check for the job status:
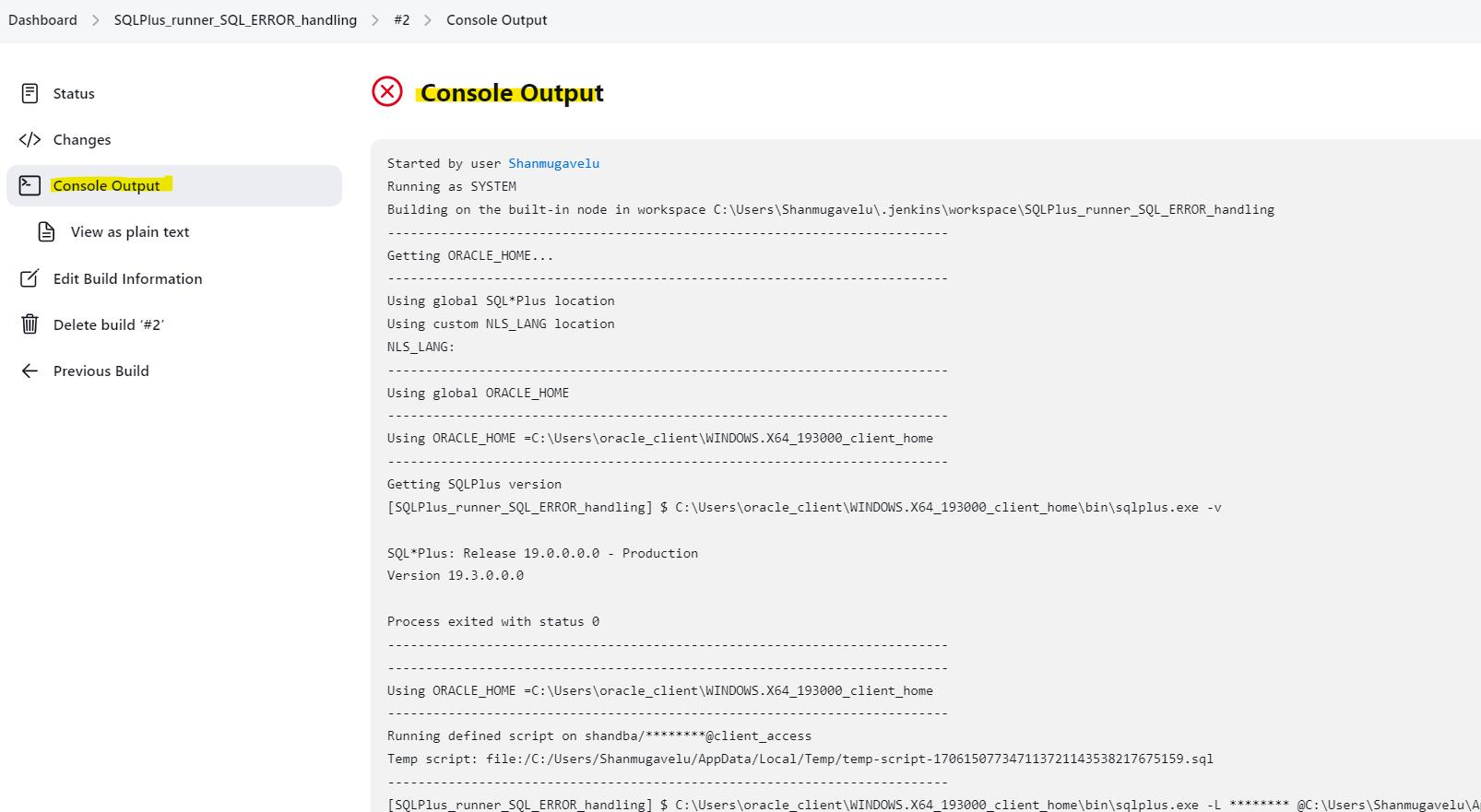
👉 Check the console output for ERROR:
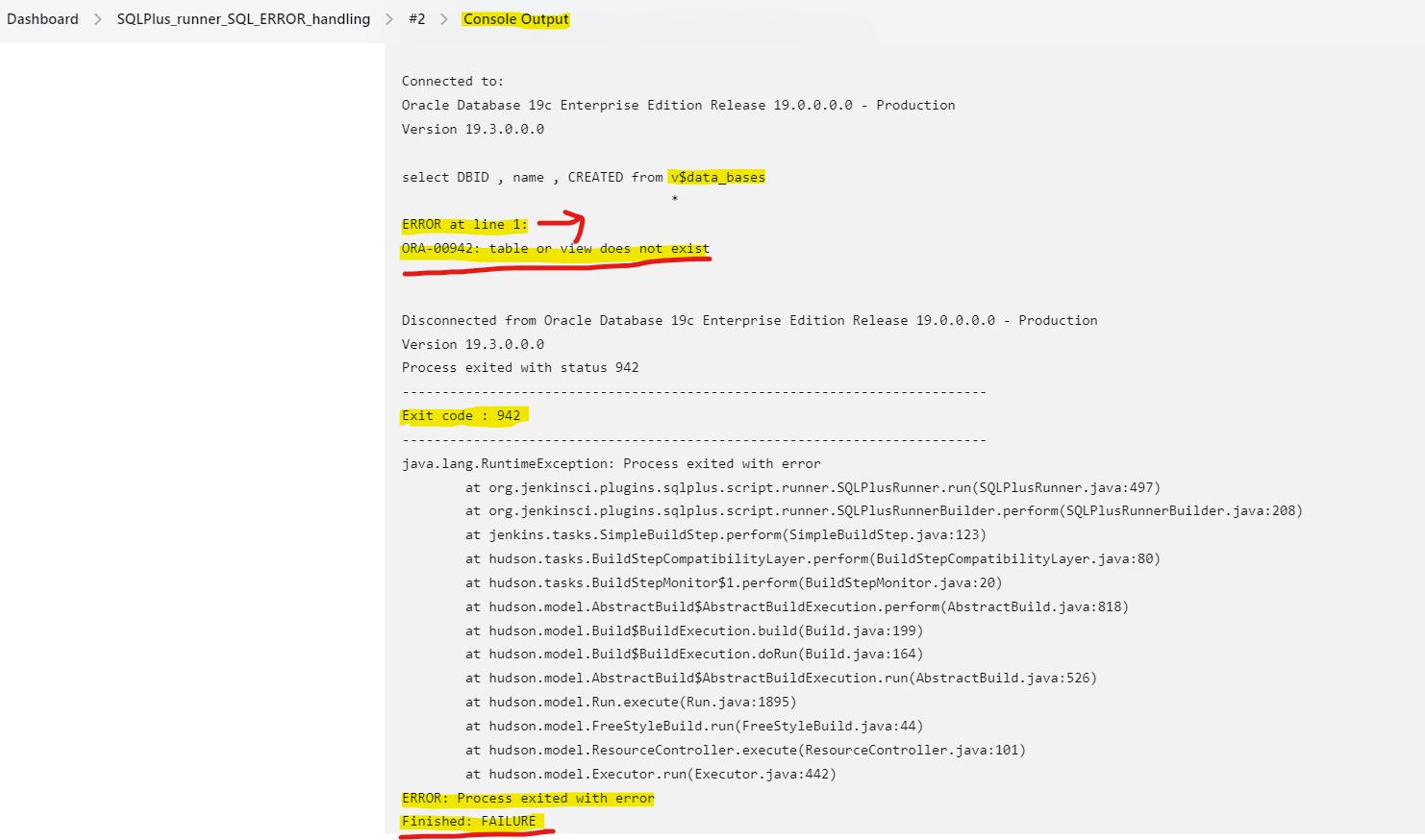
👉 Console output: continued
Known Issues: – Reported problems for SQL Plus Runner
KNOWN ISSUE 1:
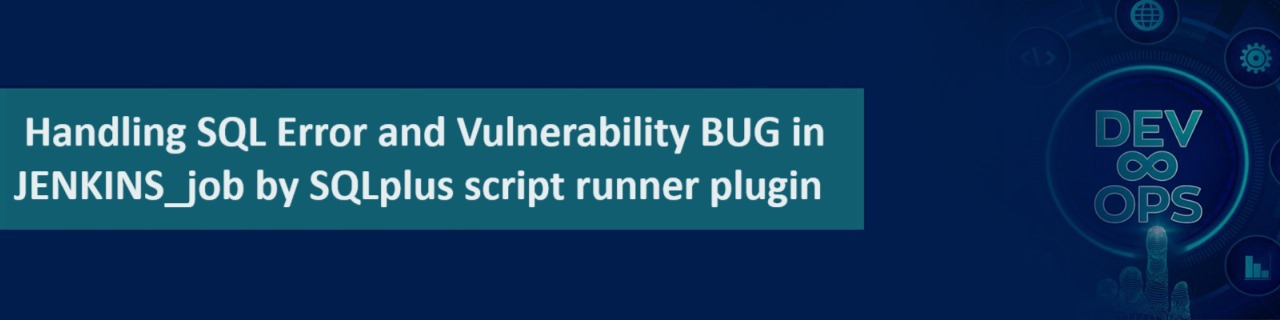
my script takes forever to execute…
▪️ Windows users sometimes get a running script stuck on build, even though they run everything on Oracle.
▪️ In that case you should use BuildTime Outplugin together to get everything working fine.
▪️ This plugin allows you to automatically terminate a build if it’s taking too long.
▪️ NOTE: This plugin isn’t applicable to pipelines.
▪️ Use the timeoutstep in workflow-basic-steps
PLUGIN installation in Jenkins
👉 This plugin supports only UI freestyle jobs (not pipelines)
 Adding Time out step in Pipeline jobs
Adding Time out step in Pipeline jobs
👉 How to write Timeout step for each pipeline type
For a Declarative Pipeline (timeout for a whole job):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
pipeline { options { timeout(time: 3, unit: 'HOURS') } agent { label 'agent_name' } stages { stage('Stage_name') { steps { // ... } } } // ... } |
For a Scripted Pipeline (timeout for a whole job):
|
1 2 3 4 5 6 7 8 9 |
def call() { node('agent_name') { timeout(time: 3, unit: 'HOURS') { stage('Stage_name') { // ... } } } } |
Timeout inside a stage (for a specific action):
Declarative Pipeline
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
pipeline { agent { label 'agent_name' } stages { stage('Stage_name') { steps { timeout(time: 3, unit: 'HOURS') { sh ' ... ' echo '...' // ... } // ... } } } } |
Scripted Pipeline
|
1 2 3 4 5 6 7 8 9 10 11 12 |
def call() { node('agent_name') { stage('Stage_name') { timeout(time: 3, unit: 'HOURS') { sh '...' echo '...' // ... } // ... } } } |
KNOWN ISSUE 2:
Every time I get this error: *cannot find SQL plus *
Jenkins plugin can’t find SQL*Plus executable file.
You should do in this order:
1. Stop Jenkins.
2. Find where are sqlplus executable file (usually at $ORACLE_HOME);
3. Check if they have proper permissions (chmod 755 *).
4. Create a global environment variable ORACLE_HOME like this:
|
1 2 |
**export ORACLE_HOME=/oracle/app/oracle/product/12.1.0/dbhome_1/ ** or export ORACLE_HOME=<your-sqlplus-directory> |
5. Test your environment with: *sqlplus -v *, should return SQL*Plus version like SQL*Plus: Release 12.1.0.1.0 Production
6. Start Jenkins.
7. Use the try to detect ORACLE_HOME option.
8. Retry your SQL*Plus operation.
KNOWN ISSUE 3:
Every time I get this error: libsqlplus.so: cannot open shared object file:
No such file or directory or SP2-0667: Message file sp1.msb not found.
You should do in this order:
1. Stop Jenkins.
2. Find where are sofiles (usually at $ORACLE_HOME\lib );
3. Check if they have proper permissions (chmod 755 *).
4. Create a global environment variable LD_LIBRARY_PATH like this:
|
1 2 |
**export LD_LIBRARY_PATH=$ORACLE_HOME/lib:$LD_LIBRARY_PATH ** or export LD_LIBRARY_PATH=<your-libsqlplus-directory>:$LD_LIBRARY_PATH |
5. Test your environment with: *sqlplus -v * , should return SQL*Plus version like SQL*Plus: Release 12.1.0.1.0 Production
6. Start Jenkins.
7. Use the try to detect ORACLE_HOME option;
8. Retry your SQL*Plus operation.
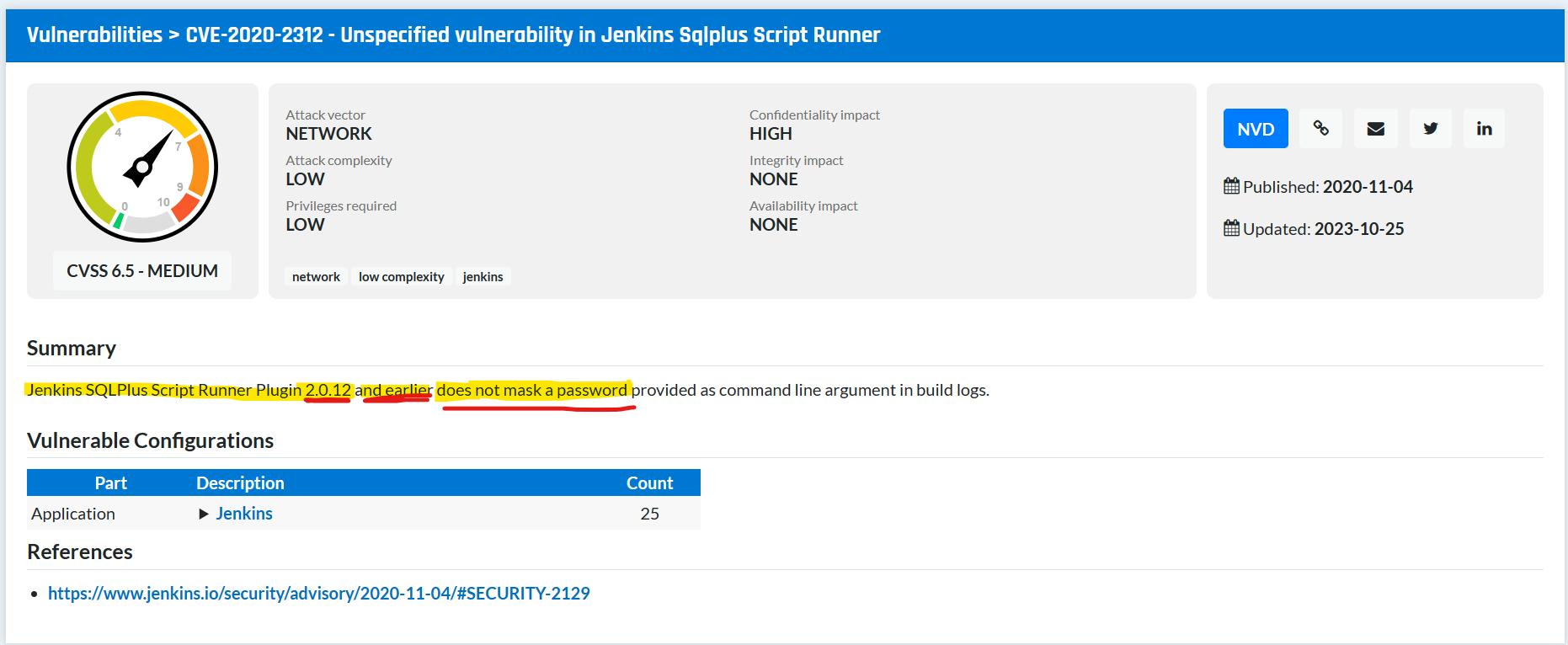
Password Vulnerability in Older version – SQL plus runner Plugin
▪️ The older version of SQL Plus script runner plugin 2.0.12 and earlier had vulnerability.
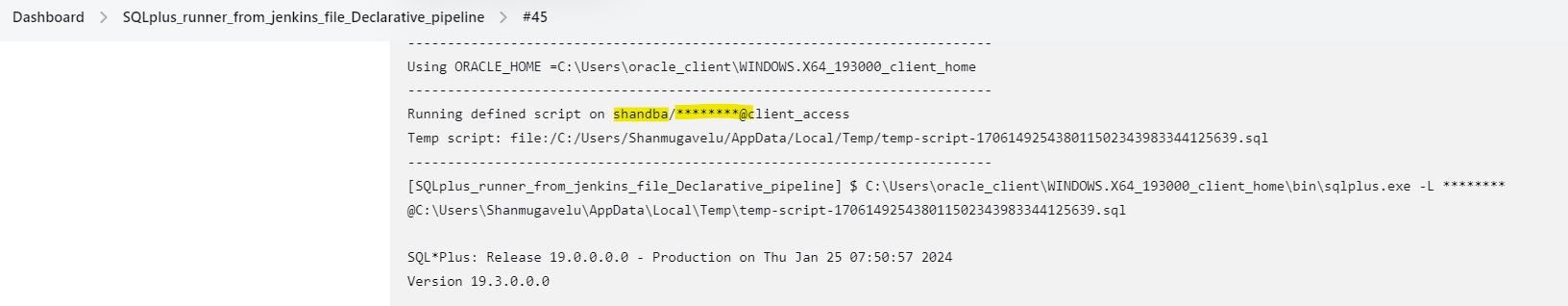
▪️ The password is not masked by Jenkins in these older versions.
▪️ The new version of Jenkins has the feature of masking the password.
👉 Password vulnerability for lower version 2.0.12:
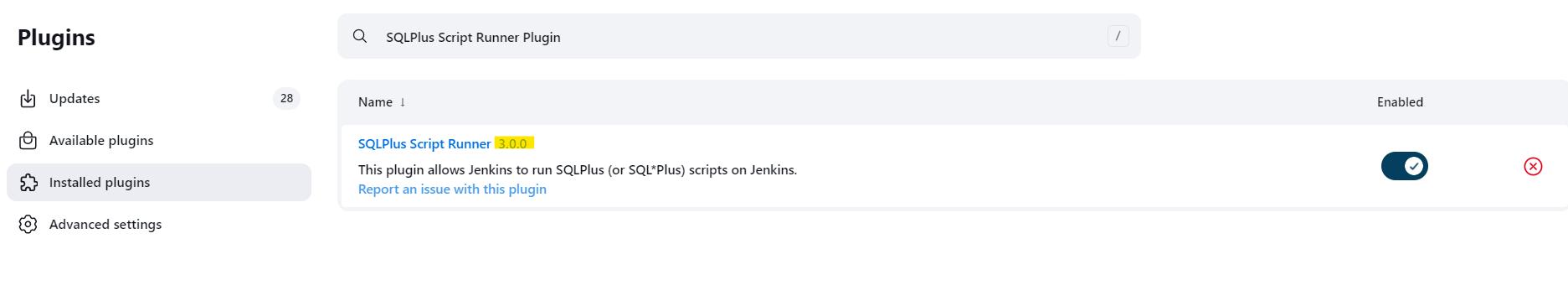
👉 The version: in our case is higher 3.0.0.
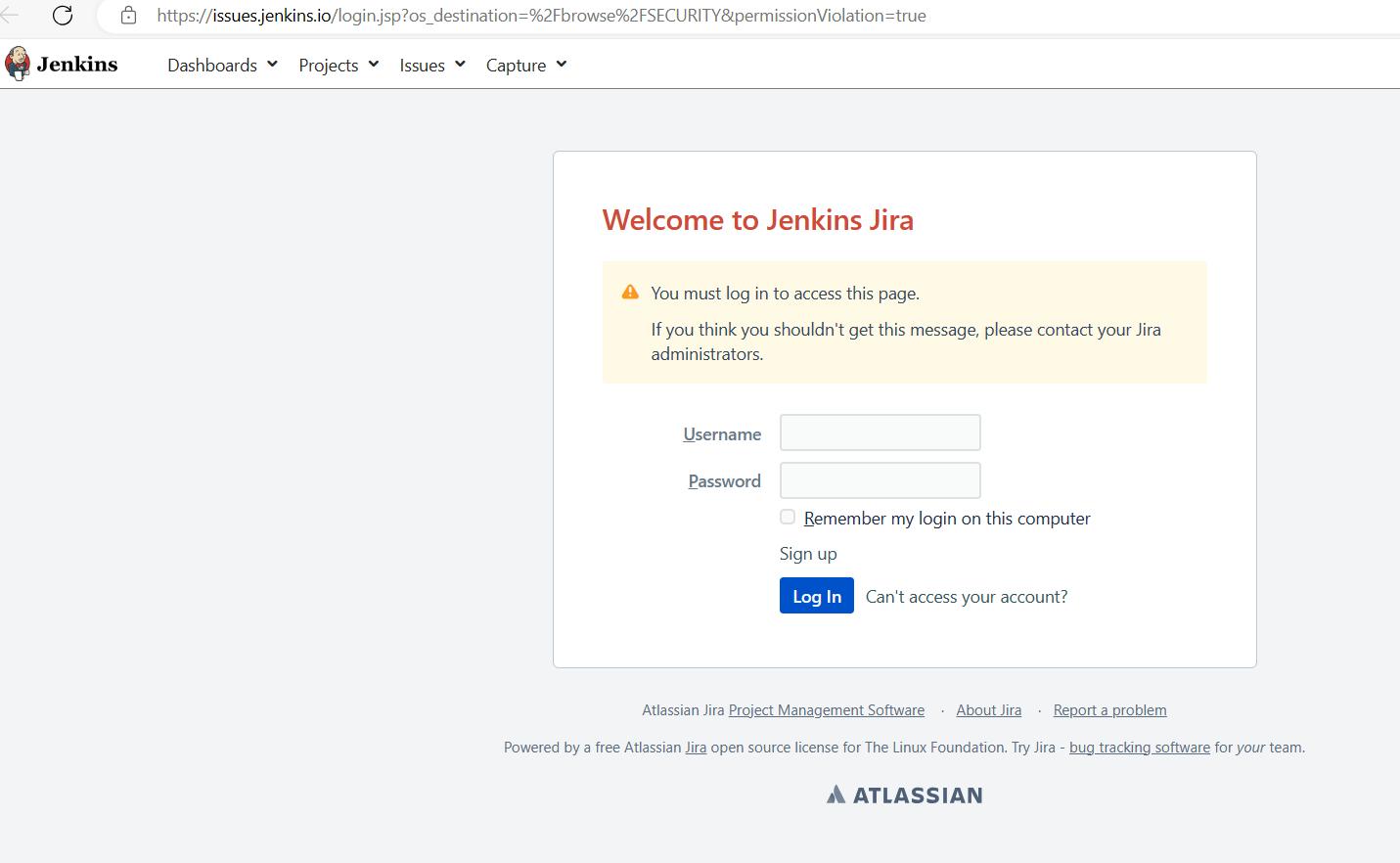
Reporting Security Vulnerabilities
▪️ Report to Jenkins security team for any vulnerability w.r.t plugin
https://issues.jenkins.io/browse/SECURITY
https://jenkins.io/security/reporting/
▪️ If you are unable to report using our issue tracker, you can also send your report to the private Jenkins security team mailing list: jenkinsci-cert@googlegroups.com
▪️ The Jenkins security team will then file an issue on your behalf and will work with the maintainers of the affected component(s) to get the issue resolved.
👉 Report a security vulnerability:
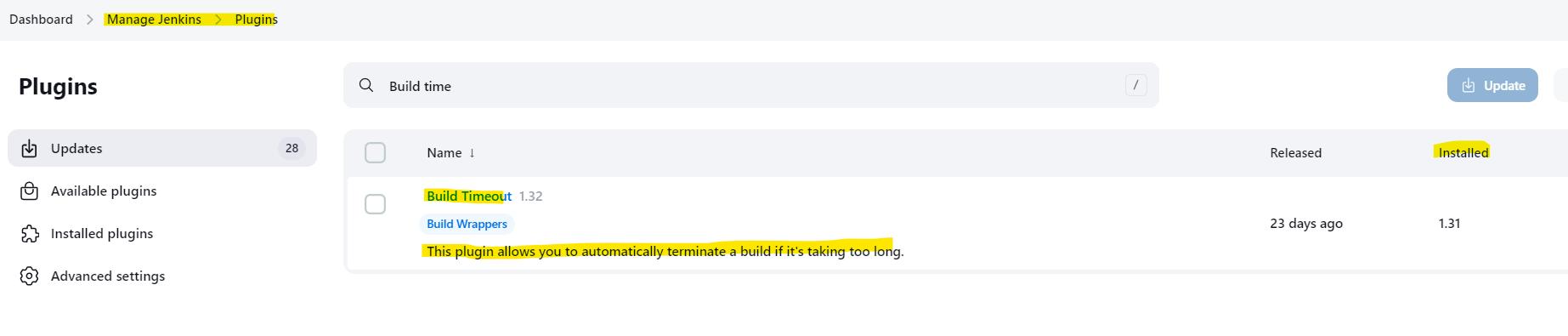
Reporting BUG -> I have a BUG to report : How to Report
▪️ Please open an open a new issue and inform https://github.com/jenkinsci/sqlplus-script-runner-plugin/issues/new
▪️ Please provide below details
▪️ sqlplus-script-runner-plugin version.
▪️ Jenkins server Operation System.
▪️ Jenkins version.
▪️ Where SQL Plus Script Runner is running (local machine or slave machine);
▪️ Slave machine Operation System (if applicable);
▪️ Oracle Database version.
▪️ Oracle SQL*Plus version.
▪️ Build log with debug info enabled.
👉 To report a bug:
Author : Venkat Vinod Kumar Siram
LinkedIn : https://www.linkedin.com/in/vinodsiram/
Assisted by Shanmugavel
Thank you for giving your valuable time to read the above information. Please click here to subscribe for further updates.
KTExperts is always active on social media platforms.
Facebook : https://www.facebook.com/ktexperts
LinkedIn : https://www.linkedin.com/company/ktexperts/
Twitter : https://twitter.com/ktexpertsadmin
YouTube : https://www.youtube.com/c/ktexperts
Instagram : https://www.instagram.com/knowledgesharingplatform
Note: Please test scripts in Non Prod before trying in Production.